It was May 21, 2014. E-commerce juggernaut eBay shocked the world by announcing that a database containing users’ encrypted passwords and other personal data was breached between late February and early March that year. Approximately 145 million user records were compromised. Those user records contained names, e-mail addresses, mailing addresses, phone numbers, birth-dates, and encrypted passwords. And there have been many more since.
Cyberattacks are an unfortunate reality of the e-commerce industry. Almost every e-commerce business – small, medium or large – is, sadly, a target for hackers and cybercriminals ready to exploit every opportunity to secure sensitive data – often, to make easy money.
The damage that cyberattacks can have on an online storefront’s brand, reputation, and revenue, is catastrophic. They can cause an immediate loss of user loyalty, especially if the user is directly affected by the attack.
Hackers are Becoming Smarter
Common cyberattacks on e-commerce sites include account takeovers, hijacked gift cards, DDoS attacks, phishing, and malware. (Read this blog for a quick summary on the different kinds of attacks that can plague e-commerce businesses.)
These attacks, and the cybercriminals perpetrating them, are becoming smarter and more sophisticated. Cybercrime doesn’t just involve stealing data, it can also be used to impact the uptime of vital systems by breaching the system through sophisticated malware or by targeting the application layer.
Recently, application layer attacks have become a favorite for attackers as most of the customer information sits at this layer. The application layer is the hardest to defend; it’s also the most exposed to the outside world. Moreover, as online stores migrate to the public cloud, the attack surface area of applications increases significantly.
Application layer attacks are usually part of multi-vector DDoS attacks, targeting not only applications, but also the network and bandwidth. Attackers target a web server, or an application server, and flood it with just enough traffic to take it offline. In the case of a web server, it involves sending hundreds of thousands of HTTP requests per second. These attacks are also smaller and not noticeable until it’s too late.
The security solutions in the market today, usually content delivery networks (CDNs) or web application firewalls (WAFs), only partially address the problem. They only take care of security at the “edge”, where user traffic commences its journey to the origin, but not the application infrastructure itself.
So how can you outsmart the most sophisticated hackers and protect your online storefront?
The answer is 360-degree security – security at the origin and security at the edge.
Webscale CloudEDGE Security
It’s why we have launched Webscale CloudEDGE Security, the industry’s first security solution that offers 360-degree protection for web application infrastructure.
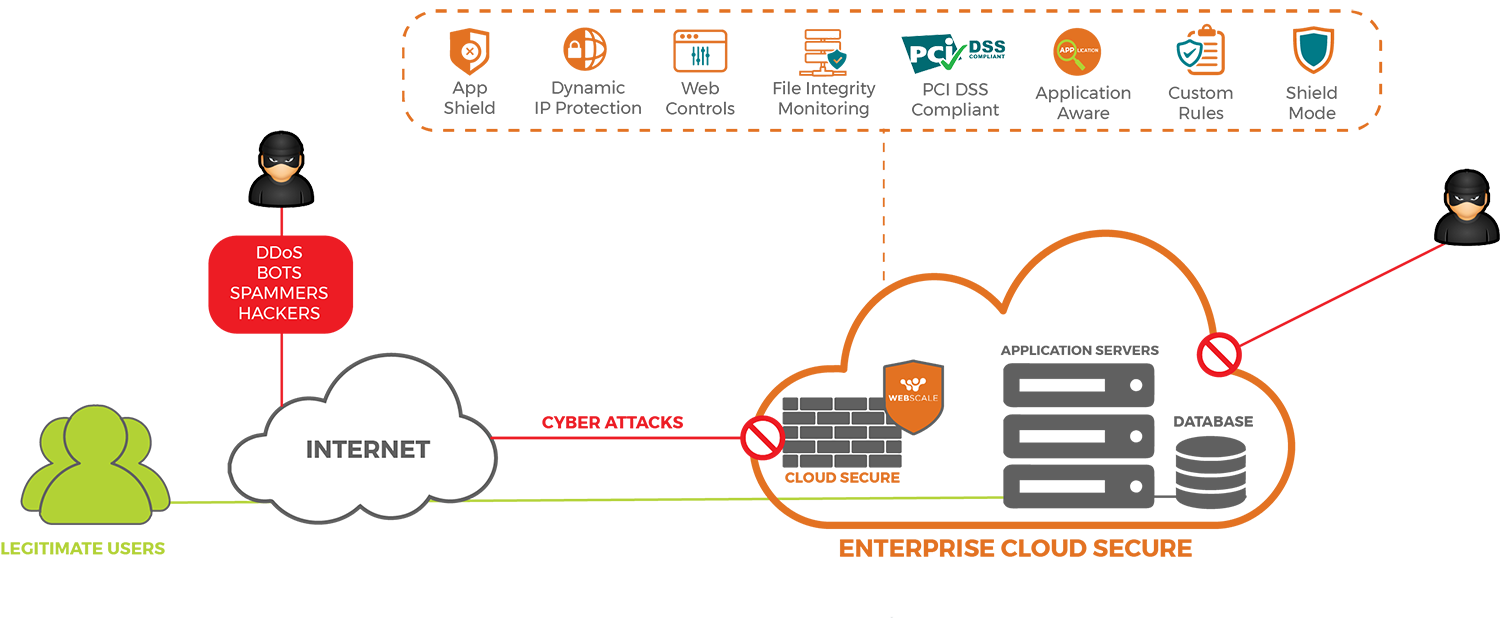
Key Features and Functionality:
- Application Awareness: Webscale CloudEDGE Security includes the only WAF designed with application awareness, including specific optimizations for e-commerce and enterprise web applications. Each application may have different security needs and the ability to apply custom security policies is critical for application owners and IT. Webscale CloudEDGE Security enables pre-defined security rule-sets based on the application.
- Block/Allow Lists offer superior flexibility to block or allow requests and sessions by IP address, user agent or the user’s origin country.
- Rate Limiting empowers application owners to block requests for a specified duration, or rate limit resource-intensive user sessions to mitigate their impact on the overall application.
- Webscale App Shield addresses the security threat posed by attackers that know the IPs of publicly addressable application servers, enabling them to bypass WAFs and other edge security measures. App Shield ensures that only traffic coming from Webscale is accepted, rejecting all other requests and enhancing end-end security for data traffic and the application backend.
- Webscale Bot IP Shield addresses the challenge of identifying attacks when the perpetrators are using different techniques to hide their identities and activities. Webscale Bot IP Shield disables, in real-time, inbound communications from IPs known to be malicious, keeping customer infrastructure secure.
- File Integrity Monitoring (FIM) enables application owners to get alerted to any changes to files or content. This helps mitigate zero-day attacks that can start with the insertion of an executable file in the backend infrastructure. Once alerted, Webscale can take many actions including adding any traffic requesting the file to a block list, or quarantining suspect servers and replacing them.
- Web Controls are the ultimate do-it-yourself custom policies that makes it easy to configure complex security protocols in an easy-to-use interface. Webscale automatically includes rule-sets specifically fine-tuned for many applications, including online storefronts.
- Shield Mode offers single-click protection when under a Distributed Denial of Service (DDoS) attack. By instantly forcing a challenge that only humans can validate, bots are immediately turned away even if they are coming from multiple sources with no easily identifiable patterns.
Check out this datasheet if you’d like to learn more about Webscale CloudEDGE Security, or reach out to us at sales@webscalenetworks.com if you’d like to speak with one of our e-commerce specialists.